Keyshield SSO
Single SiGn ON Solution
What is KeyShield SSO?
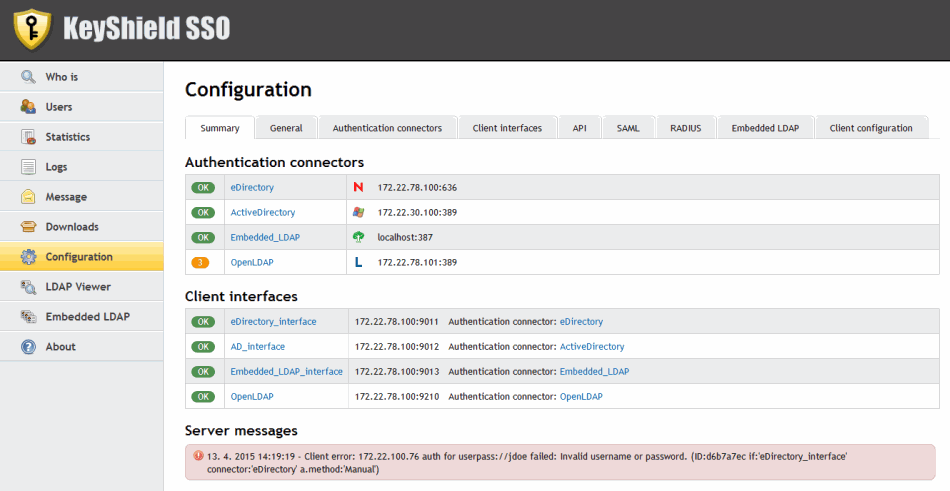
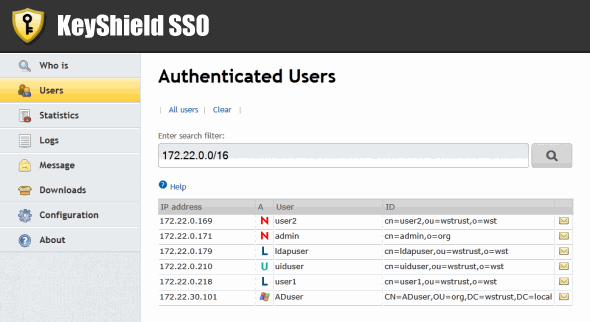
KeyShield SSO is a real SSO solution which detects and provides the identity of network users based on their authentication to eDirectory, Active Directory or LDAP (via KeyShield SSO client). Once a user is authenticated, KeyShield SSO verifies his/her identity and keeps the information about the IP address and full name of the user (see figure left). If the user then tries to connect to some information system, the identity is checked by querying KeyShield SSO based on IP address. If the user is known, no further authentication is required. This approach is more effective and safer than the way it works for example with an Internet browser that stores names and passwords, which have been used for authentication.UNIQUE FEATURES
Can handle thousands of authentications per second
Supports Non-Browser Apps through clients for many desktop and mobile platforms
Works with Multiple external LDAP sources at once or can use an internal directory
You can set up KeyShield to authenticate you against your directory – we support eDirectory, Active Directory and OpenLDAP. You can even connect multiple directories and KeyShield will then perform load balancing to distribute queries among them. If you do not have any directory, you can use KeyShield’s embedded directory service.
Built-in integration with many common systems - CMSs, DMSs and messaging
You can download plugins for many popular applications and systems, for example, GWAVA, Filr, Vibe, Drupal, WordPress and many others. Here’s a complete list of available integrations.
integration for other systems can be easily developed through RESTful API and SAML
Support for other systems can be programmed very easily and efficiently using our RESTful API. We also offer SAML conformity for systems supporting it (like Google Apps or Microsoft Office 365). In most cases, your programmer should be able to implement KeyShield for your system within one working day.
Two-factor authentication via Hardware Cards
For an additional layer of security, you can require users to place a hardware card into a card reader while they log in. This two-factor authentication can be switched on for selected services.
Supports RADIUS accounting and connects with other SSO systems
KeyShield can act as a RADIUS Accounting client – we inform active network elements (FortiGate, Cyberoam, SonicWall, SmoothWall, LightSpeed, LiteSpeed, etc.) about the identity of the user. KeyShield can also act as a RADIUS Accounting server – in which it obtains information about the identity of the user from a firewall or Wi-Fi access point after successful authentication into a VPN.
Delivery of instant messages directly to the screens of users
So-called yellow message functionality can deliver prompts to the screens of logged-in users. Such a message is hard to miss and does not go away until the user accepts it. The addressee of the message can be a specific user or a whole subnet. This function is especially suitable for sending information about network maintenance, etc.
Deployment In a working day
KeyShield SSO server is pure JAVA application which needs nothing more than JVM on Linux or Windows and an LDAP interface of eDirectory, Active Directory or LDAP. The whole installation is completed in less than a minute thanks to a comfortable installation script/MSI package. KeyShield SSO client for Windows workstations is provided as an MSI package and can be deployed manually or automatically by a solution like ZENworks. The Linux client is available in form of RPM and DEB package. The Android client is available thru Google Play market. Mac, iPad and iPhone clients are available through the Apple AppStore.
Integration In a working day
Virtually any application can be integrated with KeyShield SSO. KeyShield SSO provides HTML REST interface, a comfortable API library for "unique user ID" and maintenance of the NetworkAddress LDAP attribute as well as interactive administrator interface. Full integration is provided for CAS from JASIG and for the Security module of popular Spring framework. If your application is using Spring Security, such as the Liferay portal, the integration is included already.
Advantages
Users do not have to remember dozens of usernames and passwords, so do not endanger security by writing them on pieces of paper stuck to their monitors. It is not necessary to synchronise the login data between systems with different levels of security and threaten the security by leakage from the less secure systems. No further waste of time and money – users can access network systems instantly, manual authentication is not necessary, nor is the updating of multiple systems when regular updates of passwords occur.